Differences between TCP and UDP
TCP (Transmission Control Protocol) and UDP (User Datagram Protocol) are essential protocols utilized in laptop networking to facilitate communique among devices. Both protocols operate at the transport layer of the OSI model and play crucial roles in transmitting data across networks. While they share some similarities, they have distinct characteristics that make them suitable for different types of applications.
Transmission Control Protocol (TCP):
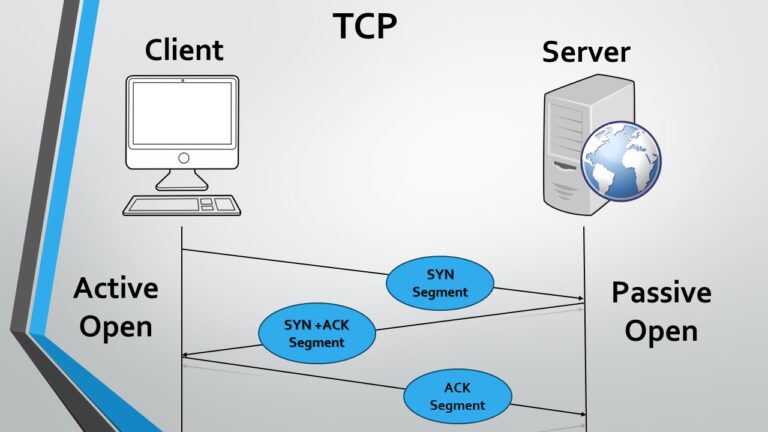
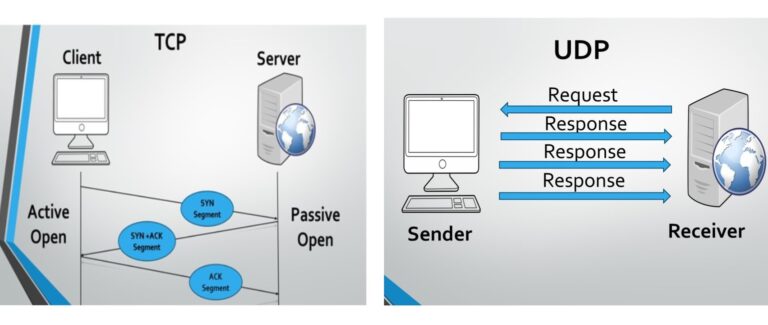
- Connection-Oriented: TCP is connection-oriented, there is an established connection between sender and receiver a connection should be there to be established before data transfer occurs. This provides stable communication free from errors.
- Reliability: TCP ensures that data is received in the order in which it was sent, and without any loss along the way. It accomplishes its reliability using acknowledgments and retransmission.
- Flow Control: It is a mechanism used by TCP to control the rate of data transmission from source to destination, in order to avoid congestion to the network and to make its traffic more efficient.
- Error Checking: TCP has robust error-checking capabilities and use of checksum and acknowledgment messages to detect and correct errors in a data stream.
- Applications: TCP is suitable to applications that need a reliable connection, such as file transfer (FTP), email (SMTP), web browsing (HTTP).
- Stateful Connection: TCP has stateful connection while data exchange. This means the sender and the receiver both know the state of each other so that the data can stay in sync and a reliable communication can be established.
- Three-Way Handshake: A connection between a client and server in TCP is established in a process that takes three steps. This is a 3-way handshake that is being set up between the sender and the receiver – this handshake is making sure that both the sender and the receiver are ready to send data out.
- Congestion Control: TCP uses advanced congestion control algorithms in order to maintain network congestion and avoid packet drop. It dynamically changes the transmission power according the network condition to enhance performance.
- Windowing: TCP uses sliding window to do flow control, i.e., allowing the sender to send multiple packets before waiting for an acknowledgement. This improves data transfer efficiency by reducing the cost of sending expanded acknowledgements.
- Security Features: With use of security protocols such as TLS, data can be transmitted over through TCP by being kept private and secure. This makes it excellent for secure internet communication.
User Datagram Protocol (UDP):
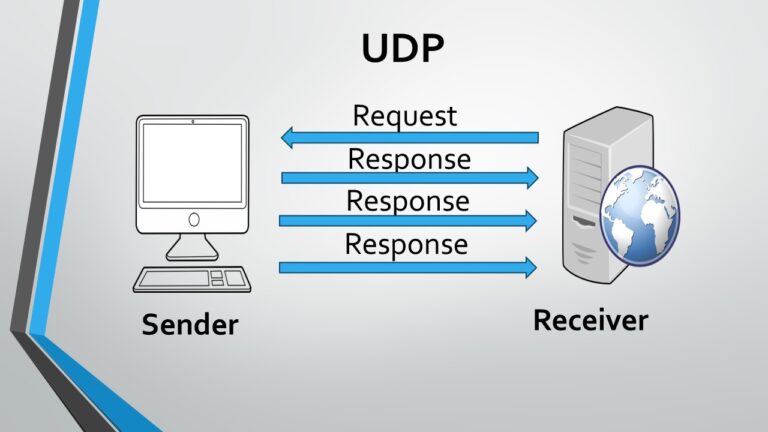
- Connectionless: UDP is a connectionless protocol, meaning that it does not establish a connection before transmitting data. Each packet is sent independently, and there is no guarantee of order or delivery.
- Unreliable: UDP provides no assurance of dependable data delivery. It does not use acknowledgments or retransmissions, making it faster but less reliable compared to TCP.
- Low Overhead: UDP has lower overhead compared to TCP because it lacks the extensive error-checking and flow control mechanisms. This makes it suitable for applications where speed is prioritized over reliability.
- Broadcast and Multicast: UDP is commonly used for broadcasting and multicasting, where the same data needs to be sent to multiple recipients simultaneously.
- Applications: UDP is often employed in real-time applications such as online gaming, streaming media (UDP-based RTP), and Voice over IP (VoIP), where low latency is crucial.
- Connectionless Nature: UDP’s connectionless nature makes it suitable for scenarios where quick data transmission is essential, and occasional packet loss is acceptable. Real-time applications, like online gaming, benefit from this characteristic.
- No Handshake: Unlike TCP, UDP does not involve a formal handshake process. This simplifies the communication setup, reducing latency, but it also means there is no inherent acknowledgment of successful packet delivery.
- Minimal Header Size: UDP has a smaller header size compared to TCP, resulting in less overhead. This makes UDP a lightweight protocol, beneficial for applications where conserving bandwidth is a priority.
- Broadcast and Multicast: UDP supports broadcast and multicast communication, enabling efficient data distribution to multiple recipients. This is valuable in scenarios where a single source needs to reach multiple destinations simultaneously.
- Low Latency: Due to its minimalistic approach, UDP is favored in applications where low latency is critical. Real-time communication, such as live video streaming or online voice chats, benefits from UDP’s ability to quickly transmit data without the delays associated with connection establishment.
Choosing Between TCP and UDP:
When deciding between TCP and UDP for a particular application, it’s essential to consider the specific requirements and constraints. If reliability, order, and error correction are crucial, TCP is the preferred choice. However, for applications prioritizing speed, low latency, and where occasional data loss is acceptable, UDP offers a more suitable alternative.
In many cases, applications may leverage both protocols within the same system to optimize performance based on the nature of the data being transmitted. This hybrid approach allows developers to strike a balance between reliability and speed, tailoring the communication protocol to the unique demands of their application.
Port Number
TCP (Transmission Control Protocol) and UDP (User Datagram Protocol) are transport layer protocols that use port numbers to facilitate communication between devices on a network. Port numbers facilitate the routing of incoming data to the relevant application or service operational on a device. Here are some common port numbers associated with TCP and UDP:
Common TCP Port Numbers:
HTTP (Hypertext Transfer Protocol): Port number- 80
- Default port for unencrypted web traffic.
HTTPS (Hypertext Transfer Protocol Secure): Port number- 443
- Default port for secure, encrypted web traffic using SSL/TLS.
FTP (File Transfer Protocol): Port number- 21
- Utilized for transferring files between a client and a server.
SSH (Secure Shell): Port number- 22
- Provides secure remote access to a system.
Telnet: Port number- 23
- Used for remote terminal access.
SMTP (Simple Mail Transfer Protocol): Port number- 25
- Responsible for email transmission.
DNS (Domain Name System): Port number- 53
- Resolves domain names to IP addresses.
POP3 (Post Office Protocol version 3): Port number- 110
- Retrieves emails from a mail server.
IMAP (Internet Message Access Protocol): Port number- 143
- Handles the management and retrieval of emails from a mail server.
HTTPS (Alternative): Port number- 8080
- Commonly used as an alternative to port 80 for web traffic.
Common UDP Port Numbers:
DNS (Domain Name System): Port number- 53
- Resolves domain names to IP addresses.
DHCP (Dynamic Host Configuration Protocol): Port number- 67 (Server) / 68 (Client)
- Automatically assigns IP addresses to devices on a network.
TFTP (Trivial File Transfer Protocol): Port number-69
- Used for simple file transfers.
SNMP (Simple Network Management Protocol): Port number- 161 (Agent) / 162 (Manager)
- Facilitates network management and monitoring.
NTP (Network Time Protocol): Port number- 123
- Aligns the clocks of devices within a network for synchronization.
Syslog: Port number- 514
- Collects and forwards log messages in an IP network.
SSDP (Simple Service Discovery Protocol): Port number- 1900
- Discovers and advertises network services.
DNS (Alternative): Port number- 5353
- An alternative port for DNS service, commonly used in multicast DNS (mDNS).
QUIC (Quick UDP Internet Connections): Port number- 443
- A modern, secure transport protocol developed by Google.
RADIUS (Remote Authentication Dial-In User Service): Port number-1812 (Authentication) / 1813 (Accounting)
- Authenticates and authorizes network users.
These port numbers represent only a subset of the well-known ports, and many others are designated for various applications and services. It’s important to note that these assignments are not strict, and some applications may use different ports based on configuration. Additionally, ports in the range of 49152 to 65535 are designated for dynamic or private use and are not officially assigned to specific services.
Conclusion:
In summary, TCP and UDP serve different purposes in network communication. TCP ensures reliability, ordered delivery, and error correction, making it suitable for applications where accuracy is paramount. On the other hand, UDP sacrifices some reliability for speed, making it ideal for real-time applications that prioritize low latency over error-free transmission.
Understanding the characteristics of TCP and UDP is essential for designing efficient and reliable network communication systems tailored to the specific requirements of different applications.
